Crysis is a highly risky ransomware virus. Crysis can be covertly installed on its target computer. This virus locked your PC and prevents you from accessing all stored files. It extends the name of all encrypted files by adding the .crysis extension. After encryption, it displays a message containing email address and on how to regain access to all encrypted files.
Just like all other ransomware virus, Crysis demand to pay for certain amount in order to decrypt your files. This is in exchange for the private key that holds by malware authors. It says that merely paying the demand will let you regain access to your files. In order to pay the ransom, you have to contact crooks through email at dalailama2015@protonmail.ch. Or you may use the email goldmanO@india.com if you havenít received any response from the first email within 48 hours. You may expect then from their response the amount of ransom, when to be paid, and how to pay it.
Please keep in mind that paying the ransom is not the key to decrypt your files. Cyber crooks only give you false hopes. Paying the ransom would not lead to your files being returned. It was just like spending your money for nothing. One thing is certain about Crysis virus; malware author will get the money and gives you nothing in return. This is how Crysis really works. Crysis was made to extort money from its victims.
Crysis is just the same among countless number of ransomware-type viruses which retrieval of data is absolutely not implemented as promised. They are all the same in terms of locking the computer and ends up only in collecting the ransom.
Threat Summary
| Threat: | Crysis |
| Type: | Ransomware |
| Brief Description: | This ransom virus encrypts selected files on the computer and prompts user to pay for decryption key. |
| Protection Tool: | ‚Ėľ DOWNLOAD MalwareFox |
Description
Crysis is a highly risky ransomware virus. Crysis can be covertly installed on its target computer. This virus locked your PC and prevents you from accessing all stored files. It extends the name of all encrypted files by adding the .crysis extension. After encryption, it displays a message containing email address and on how to regain access to all encrypted files.
Just like all other ransomware virus, Crysis demand to pay for certain amount in order to decrypt your files. This is in exchange for the private key that holds by malware authors. It says that merely paying the demand will let you regain access to your files. In order to pay the ransom, you have to contact crooks through email at dalailama2015@protonmail.ch. Or you may use the email goldmanO@india.com if you havenít received any response from the first email within 48 hours. You may expect then from their response the amount of ransom, when to be paid, and how to pay it.
Please keep in mind that paying the ransom is not the key to decrypt your files. Cyber crooks only give you false hopes. Paying the ransom would not lead to your files being returned. It was just like spending your money for nothing. One thing is certain about Crysis virus; malware author will get the money and gives you nothing in return. This is how Crysis really works. Crysis was made to extort money from its victims.
Crysis is just the same among countless number of ransomware-type viruses which retrieval of data is absolutely not implemented as promised. They are all the same in terms of locking the computer and ends up only in collecting the ransom.
Procedures to Remove Crysis
Download FREE Removal Tool
Removal steps on this page will help you get rid of the threat effectively using tools and virus scanners. Please make sure that you will carry out the guide in exact order.
Procedure 1: Scan Computer in Safe Mode Using Installed Anti-virus Program
1. First, we will try to remove Remove .Crysis Ransomware (Virus Removal) by running a virus scan under Safe Mode with Networking. To perform this task, please complete these procedures.
Start in Safe Mode with Networking (Windows XP/Vista/7 Instruction)
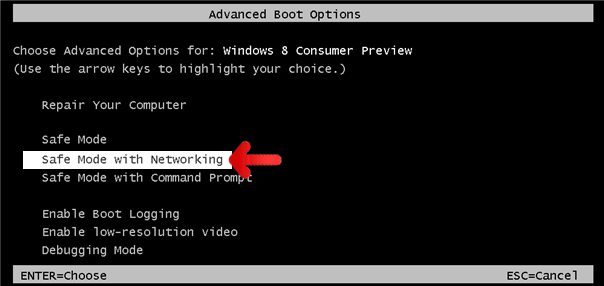
- Please restart the computer and just before Windows start, press F8 on your keyboard repeatedly. You will be presented with Advanced Options Menu.
- From the selections, choose Safe Mode with Networking. Please use keyboard's arrow up/down to navigate between selections and press Enter to proceed.
Start Windows 8 in Safe Mode with Networking
- Please restart the computer and as soon as it begins to start, please press Shift+F8 keys.
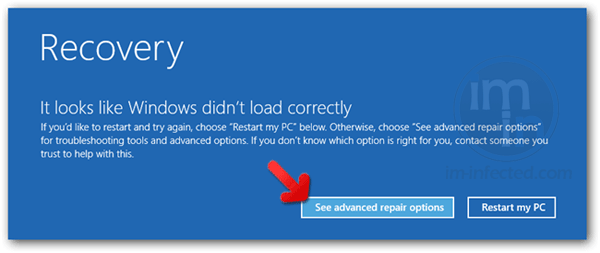
- Instead of seeing Advance Boot Options, Windows 8 will display Recovery Mode. Continue with the given steps until you reach Safe Mode function.
- Click on 'See advanced repair options'.
- Then, click on Troubleshoot.
- Next, please select Advanced options.
- On the next window, please choose Windows Startup Settings.
- Lastly, click on Restart button. Windows 8 will now restart and boot into Advanced Boot Option wherein you can run the system in Safe Mode with Networking.
2. Open your installed anti-virus programs and update it to the most recent version by automatically downloading necessary updates.
3. Thoroughly scan the computer and remove all identified threats. Do not restart or turn off the computer after the scan process. You still need to run another scan. Please follow the next procedure.
Procedure 2: Scan and remove Crysis files with MalwareBytes Anti-Malware
To remove Crysis, download Malwarebytes Anti-Malware. This tool is effective in getting rid of Trojans, viruses and malware.
1. After downloading, please install the program using the default settings.
2. At the end of the installation, please make sure that it will download necessary updates.
3. Once update has completed, MBAM will launch.
4. Select SCAN from the top menu. Then, click on Threat Scan (Recommended) section.
5. Click on Start Scan to thoroughly scan the computer. Remove all threats detected by this anti-malware program after the process.
Procedure 3: Run Microsoft Safety Scanner to remove Crysis components.
MS Safety Scanner is a free security tool that offers on-demand virus scanning and helps remove threats from the infected computer. It is a stand-alone program that works even with existing antivirus program.
Important: Each download of Microsoft Safety Scanner expires 10 days after the acquisition date. If this period lapses, you need to download the same program from the same location again. New download contains newer virus definition and database to detect and clean most recent viruses.
To use this tool in removing Crysis, please follow this procedure.
1. Download Microsoft Safety Scanner from official web site. Click on the button below.
2. Save the file to a convenient location such as Desktop.
3. Once the download completes, browse the folder and double-click on the file msert.exe. Icon for this file looks like this.
4. If Windows prompts for a security warning and ask if you want to run the file, click on Run. For Windows Vista/7 users, you may right-click on the file and select Run as administrator from the selection.
5. On initial run, the tool will display End User License Agreement, please accept the terms and click Next. Continue on the process until you reach the Scan Type window.
6. Select on Full scan to entire the system and detect any presence of Crysis. Then, click Next button to begin the scan process. Scanning may take a while, please be patient.
7. Once Microsoft Safety Scanner finished on scanning the computer, it will display the result. If it finds presence of Crysis and other malware, the tool removes them automatically.
8. Click on Finish button to close the tool.
Recover Crysis Encrypted Files
Crysis Decryption Tool
1. Download Kaspersky RakhniDecryptor version 1.17.8.0 or later from this official website link.
2. After downloading, extract the file to a folder on your hard drive.
3. Locate RakhniDecryptor.exe tool and double-click to launch the scanner.
4. Before we begin, make sure that you have downloaded the correct version. Click on program Title or About link to verify. It should be 1.17.8.1 or later because older version of the tool does not support .Crysis encrypted files.
5. Click on Start Scan to initiate the process. RakhniDecryptor will prompt you to specify path to encrypted files.
6. Navigate to folder containing .CrySis file and select specific type such as .XLS, .DOC, .JPG, and so on. TEXT file should not be selected as there were reports of decryption problem when selecting this file type.
7. When done with the selection, please click Open button. RakhniDecryptor will use your chosen file as a patter to scan remaining encrypted .Crysis files. This process may take a while. Please wait for the scan to finish.
8. Once done with the scan and decryption, RakhniDecryptor will display scan results including numbers of scanned items and productively decrypted.
9. You can click on Details to view specific details of recovered files. See image below for reference.
Use ShadowExplorer to Recover Files
Recovering Crysis encrypted files using this tool may only be possible if the virus did not erased the Shadow Copies of files on your computer. Volume Shadow Service is a Windows feature and is a component of Windows Backup and System Restore. Backup data are kept automatically in the system after enabling System Restore. Therefore, you may never use this feature when System Restore not active on the computer.
1. Download the most recent version of ShadowExplorer from their official website. Click the button below.
2. Install this program on your computer. It should initialize after the installation process. You may also double-click the created icon to run ShadowExplorer.
3. On main interface, click on the Drive Path at upper left corner to list all Volume Shadow Copies kept on your computer.
4. Select preferred time and date you wish to restore. It is suggested to select the most recent copy before the Crysis infection.
5. Right-click on the folder you wish to restore. Then, click on Export.
6. ShadowExplorer will prompt for the new location of files to recover. Please specify the path where you want to save copies of your files.